Basic single sign on requirements (checklist)
It’s critical that your SSO solution meets the basic requirements to support employees and IT needs. That means a secure solution and one with high usability. But remember that SSO is only part of your identity and access management solution. Digital transformation today relies on an Identity and Access Management (IAM) platform that includes SSO as well as other tools like MFA and directory integration.

Use the checklist below to make sure that your SSO system offers the protection your company needs.
User community support
Does the SSO solution support all your user communities?



Customers
If your customers need access, does the SSO system support commonly-used consumer authentication methods?


True SSO
Does the SSO solution allow true single sign-on versus password vaulting?


Application integration
Does the SSO solution work with your cloud and on-prem apps?


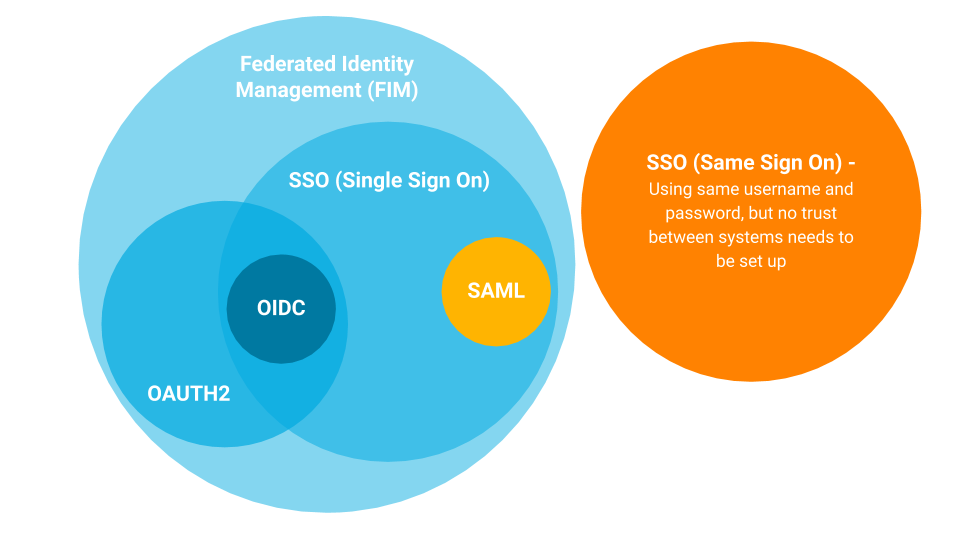
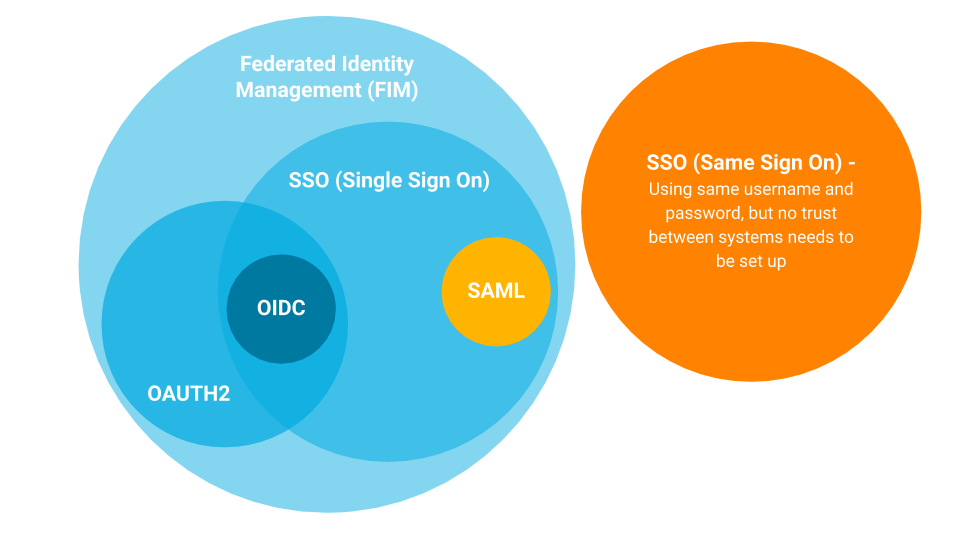
Open standards support
Does the SSO solution support the most common, widely-used protocols that enable a trusted relationship?




Reputation for security
Does the vendor meet the common, highest security standards and implement adequate internal processes?














Availability and disaster recovery
Does the SSO service demonstrate consistent and high availability and the ability to recover quickly from disasters?




High usability
Is the SSO user interface simple enough that employees will embrace it?





Mobile ready
Does the SSO solution provide thorough support for mobile users?



Flexible password rules
Does the SSO system support and enforce password requirements in a usable and effective manner?




Enterprise access
Does the SSO solution integrate with your network access points?



Federation
Does the SSO solution allow you to use the existing, corporate identity providers you prefer?





Authentication
Does the SSO solution provide additional security?




Developer support
Does the SSO solution provide APIs and support so you can enable single sign-on for your custom applications and third-party systems?



Reporting
Does the SSO solution provide reports that enable you to meet compliance requirements and enhance your security based on threat data?


Advanced requirements
Although any SSO solution should meet basic requirements, organizations making a successful digital transformation usually choose solutions that meet advanced requirements. An advanced SSO solution ensures, from the start, that you aren’t behind the curve.
Behavioral analytics
Does the SSO solution use behavioral analytics to intelligently adapt and respond?



Manage authorization
Can the SSO solution manage authorization through its integration with your identity provider(s)?


Easy integration
Can you integrate the SSO solution with your custom apps and in your organization without having to replace or significantly modify existing solutions?